Books You Should Read: The Hardware Hacker’s Handbook
[ad_1]
Here on Hackaday, we routinely cover wonderful informative writeups on different areas of hardware hacking, and we even have our own university with courses that delve into topics one by one. I’ve had my own fair share of materials I’ve learned theory and practical aspects from over the years I’ve been hacking – as it stands, for over thirteen years. When such materials weren’t available on any particular topic, I’d go through hundreds of forum pages trawling for details on a specific topic, or spend hours fighting with an intricacy that everyone else considered obvious.
Today, I’d like to highlight one of the most complete introductions to hardware hacking I’ve seen so far – from overall principles to technical details, spanning all levels of complexity, uniting theory and practice. This is The Hardware Hacking Handbook, by Jasper van Woudenberg and Colin O’Flynn. Across four hundred pages, you will find as complete of an introduction to subverting hardware as there is. None of the nuances are considered to be self-evident; instead, this book works to fill any gaps you might have, finding words to explain every relevant concept on levels from high to low.
Apart from the overall hardware hacking principles and examples, this book focuses on the areas of fault injection and power analysis – underappreciated areas of hardware security that you’d stand to learn, given that these two practices give you superpowers when it comes to taking control of hardware. It makes sense, since these areas are the focus of [Colin]’s and [Jasper]’s research, and they’re able to provide you something you wouldn’t learn elsewhere. You’d do well with a ChipWhisperer in hand if you wanted to repeat some of the things this book shows, but it’s not a requirement. For a start, the book’s theory of hardware hacking is something you would benefit from either way.
Having a solid theoretical basis for hardware hacking helps a lot. Don’t get me wrong, you’ll do pretty well reading our articles and learning from examples of your fellow hackers’ work – but there are going to be structural gaps when it comes to how hacks relate to each other and what else is out there.
 Traditionally, such gaps would be by universities and educational courses, taking a lot of information, structuring it and then gifting that structure for you to sort all further knowledge into. Sadly, we know that even if you can find a professor, it’s not a requirement that their lectures are engaging – or up to date with modern times. This book spends a hundred pages creating a structure for you, a categorized bookshelf to sort your books into. In order to have a complete picture of hardware and never run out of ways to approach it, it helps if you understand your device in the same way that a hardware security understand s it, and both of our authors worked tirelessly to convey their mental frameworks to you, with plentiful examples.
Traditionally, such gaps would be by universities and educational courses, taking a lot of information, structuring it and then gifting that structure for you to sort all further knowledge into. Sadly, we know that even if you can find a professor, it’s not a requirement that their lectures are engaging – or up to date with modern times. This book spends a hundred pages creating a structure for you, a categorized bookshelf to sort your books into. In order to have a complete picture of hardware and never run out of ways to approach it, it helps if you understand your device in the same way that a hardware security understand s it, and both of our authors worked tirelessly to convey their mental frameworks to you, with plentiful examples.
Whether it’s going through Intel CPU die shots and pointing out different areas, showing protocol signal traces to demystify what really happens with a signal, or explaining the potential hidden in different PCB features you might encounter on the board you’re tackling, you get a glimpse into an expert’s mind as you go through the examples they provide you with. It doesn’t shy away from topics like cryptography, either – something that a hacker might not know they could use, and might be compelled to treat as a black box. In fact, it’s arguably one of the most important topics such a book could go into – and go there, it does. Before you start RSA key extraction, they go through RSA calculations involved in cryptographic signatures – while some understanding of algebra is beneficial, it’s not required, and you can always supplement with something like the RSA calculator we covered recently.
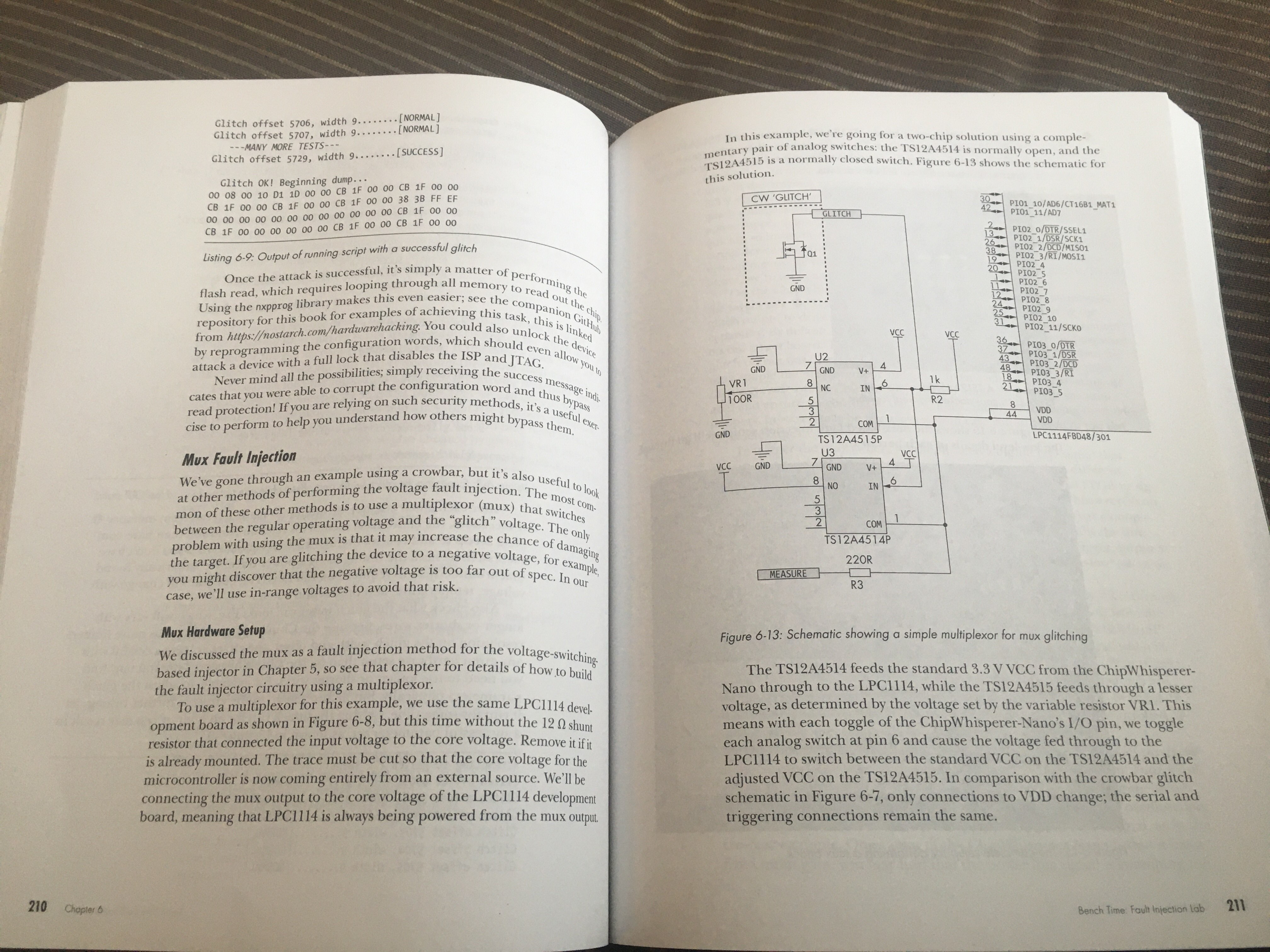
 Without a doubt, you’ll want examples, as that’s how we learn best. With these advanced techniques in hand, they take the Trezor One cryptowallet, a device sold online today, and bypass its security measures, extracting the private keys stored on the wallet. The focus on power analysis and glitching pays off handsomely here – in fact, almost literally. This demonstration is advanced and heavy enough that it deserves its own chapter, and even if you don’t follow the steps as you go through it, the attack ties the concepts you’ve seen together, helping you make the links between what you’ve read and what you will do when you need to extract secrets out of your own device.
Without a doubt, you’ll want examples, as that’s how we learn best. With these advanced techniques in hand, they take the Trezor One cryptowallet, a device sold online today, and bypass its security measures, extracting the private keys stored on the wallet. The focus on power analysis and glitching pays off handsomely here – in fact, almost literally. This demonstration is advanced and heavy enough that it deserves its own chapter, and even if you don’t follow the steps as you go through it, the attack ties the concepts you’ve seen together, helping you make the links between what you’ve read and what you will do when you need to extract secrets out of your own device.
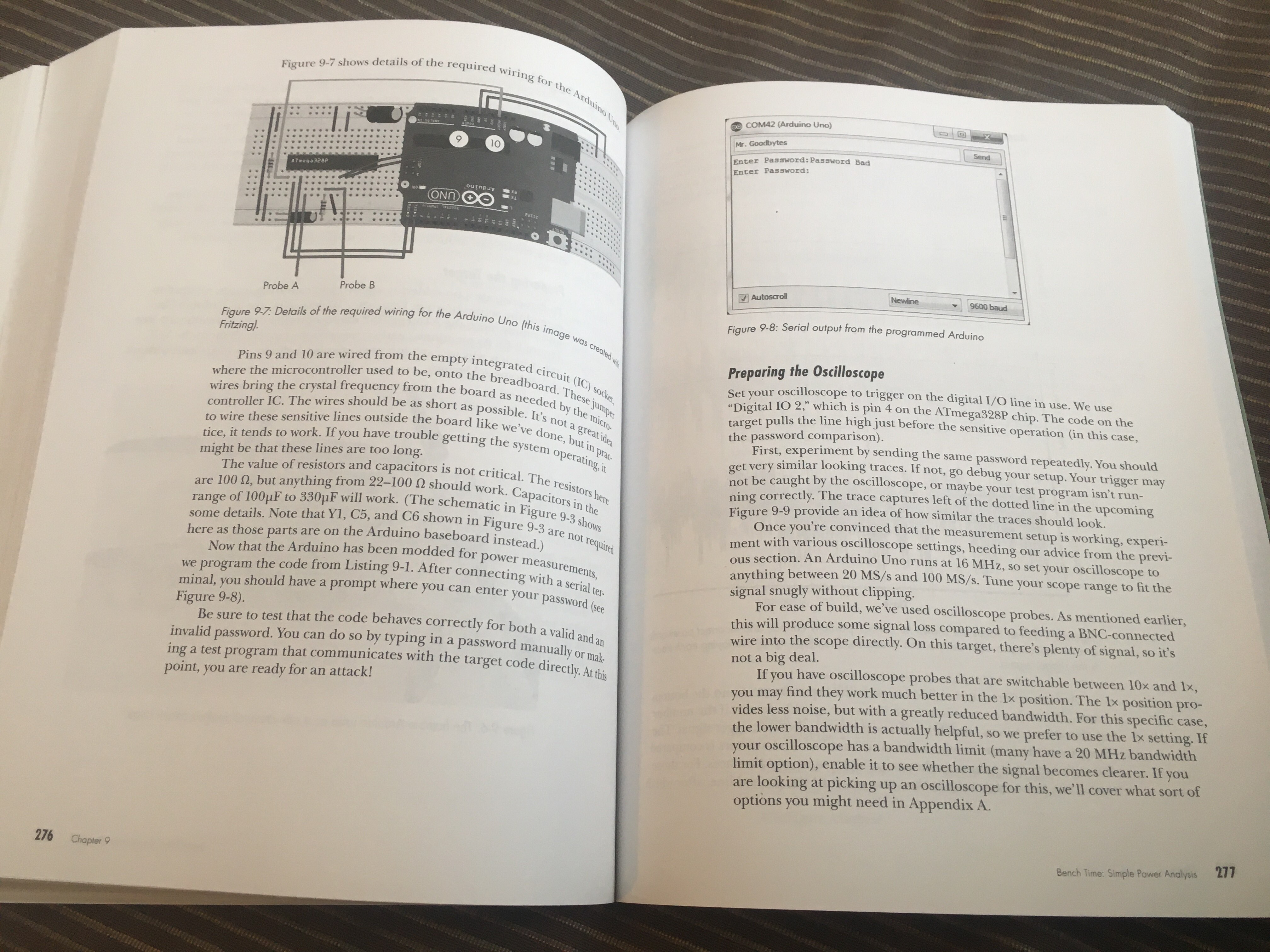
The authors make sure to keep the theory firmly coupled to real-world hardware as the book progresses. As training grounds for the Trezor wallet foray, you’ll be taught you how to solder a FET to the underside of a Raspberry Pi 3B+ PCB in order to glitch the CPU power rail and try making the CPU skip instructions. This exercise assumes you have a ChipWhisperer, though just the Lite version will do, but if you want to get real results anyway without the precise timing that the ChipWhisperer brings, you can use an ATMega328P and a piezoelectric generator from a BBQ lighter – giving you insights without tying the book’s value to a piece of extra hardware.
 Then, they go into power analysis – something that you can often do with an oscilloscope, and present you with the basics. It’s a chapter that I’m only going through myself still, with this book being as information-dense as it is. However, I have high hopes for it, as power analysis is simultaneously a relatively non-invasive way to extract information and also an attack vector that most of hardware out there in the wild is susceptible to, making this part of the book a priority of mine when facing a bit of free time in my schedule. In fact, about a third of this book is devoted to power analysis techniques, from simple to advanced, and goes through multiple test setups, with even an Arduino-based target to get your feet wet.
Then, they go into power analysis – something that you can often do with an oscilloscope, and present you with the basics. It’s a chapter that I’m only going through myself still, with this book being as information-dense as it is. However, I have high hopes for it, as power analysis is simultaneously a relatively non-invasive way to extract information and also an attack vector that most of hardware out there in the wild is susceptible to, making this part of the book a priority of mine when facing a bit of free time in my schedule. In fact, about a third of this book is devoted to power analysis techniques, from simple to advanced, and goes through multiple test setups, with even an Arduino-based target to get your feet wet.
Of course, part of hardware hacker’s power is in the equipment, which is why it’s hard to write a book like that and not expect your reader to have a few specific tools. The authors are mindful of that, which is why there’s an entire chapter going into equipping your own lab – on budgets from high to very low. A lot of the tools, you’ll be able to makeshift or repurpose, or will be able to use thanks to a friendly nearby hackerspace. Of course, most of them, you’ll get by without in the beginning, but when you encounter a particular problem, it’s helpful to know that there’s a tool for your exact need.
Since this book’s release, we’ve seen Colin advance the frontier of side channel attacks once more. Just last year, he’s given a Remoticon talk about EM injection glitching, and provided us with an accessible method on doing that without any fancy hardware requirements. These side channel attacks are an advancing field that chips will remain vulnerable to in the foreseeable future, and this book will get you up to speed on applying these methods when unlocking your own
For newcomers, such a promising field of study is a great intro to getting hardware, as many other attack surfaces we’ve known for years are nowadays well-protected and often won’t work as well in the wild. For professionals, you’ll undoubtedly find a few blind spots in your knowledge that you’d do good eliminating. We don’t have technology for uploading information into our brain – yet; as it stands, books are the closest we can get to that, and The Hardware Hacking Handbook is a respectable attempt to teach you what hardware hackers like [Jasper] and [Colin] know.
[ad_2]
Read Nore:Books You Should Read: The Hardware Hacker’s Handbook
